
In the Guide, I will inform you what using an account on the ethereum blockchain system means. I’ll also inform you on the methodology in which you can produce an address internally. Last, I will supply you with the significance of private keys and public keys.
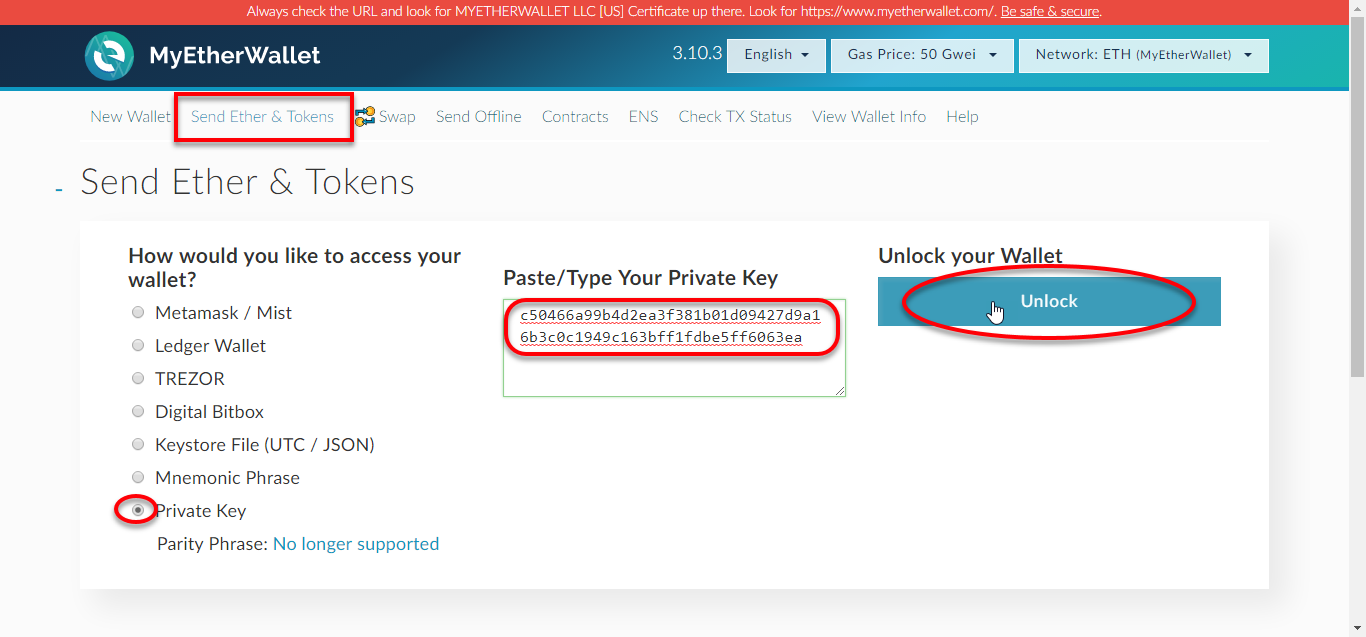
If you have an Ether account, you can send ethereum with myetherwallet out of one particular address to another. Let us have an example of you sending 1 ETH for your buddy. And the ether you’re sending isn’t in the pocket. So where are you? The ETH is found on the blockchain network. Therefore once you initiate a practice of transferring the 1 ether, you will communicate with the blockchain network to either debit or credit ether. The big issue today is the methodology where the blockchain network knows when and how to credit and debit. The cryptography process makes the latter to happen. It does so using the personal or the public keys. A personal key in the ethereum ecosystem is composed of 64 random hex characters. An individual can make his or her own personal key. It is important you notice that when creating the private key, you ought to make it random. The latter will stop someone from guessing it.
Private keys may also be created for you.
To ensure Security cases together with your eth private key myetherwallet, it is possible to encrypt it with a password. The latter is a standard security measure that ensures that your credentials are kept protected from unauthorized personnel. In the latter circumstance, once you will be opening your wallet, then you may enter the private key in addition to password. It will act as a two factor authentification system. Sometimes, you may only have to enter the passwords when sending trades. Generally, both factor authetification will be designed when you would like to perform significant transactions in your wallet.
Public keys too Provide an additional layer of protection on your pockets. They’re made from the private keys with the Elliptical Curve Digital Signature Algorithm. As its name suggests public keys are intended for the general public. They are used by many individuals within an organisation. After developing a public key within an ethereum network, it is possible to hash it using SHA3. You’ll get 6 characters long. The aftermath of this procedure is going to be 40 characters as well as also the 20 bytes. The latter are the ethereum address. It is important to note that the blockchain program is based on the private key login myetherwallet asymmetric security element. Therefore, you can use two ways to access data on the blockchain network. For example, you can get financial transaction using a personal key. Other data which aren’t privy can be obtained using another private key.
In conclusion Private and public keys ensure safety of cryptocurrencies wallets. Personal Keys are more secure than public keys. You will use private keys to generate public keys. That’s one of the differences between them.





